Projects involving information security require cyber-security experts. To become a cyber security expert, you must complete a structured process to earn the CISSP certification. CISSP specialists are in demand worldwide because they secure business information from cyber-attacks.
The process includes understanding the CISSP Body of Knowledge and passing a test.
The CISSP certification tests the applicant’s knowledge of cyber security. Professionals with experience in cyber security can attempt this test.
The CISSP certification demonstrates expertise, allowing you to further your career, and join the network of cyber-security leaders.
What is CISSP Certification?
CISSP stands for Certified Information Systems Security Professional and is a data security certification created and maintained by ISC (International Information System Security Certification Consortium), a Non-Profit Organization.
ISC developed this certification in early 1990 to create a standard certificate for information security professionals.
This is the first certification to satisfy American National Standard Institute (ANSI) ISO/IEC 17024 requirements and receive approval from the US Department of Defense (DoD) in the categories of International Assurance Technical (IAT) and International Assurance Managerial (IAM).
In the IT industry, security experts with CISSP security certification earn the highest salary, which is around 140,000 USD. This makes CISSP certification the most sought-after certification in the industry.
Professionals who want to advance their careers in cybersecurity should consider becoming CISSP certified. A CISSP-certified expert can work with cloud computing, risk management, mobile security, application development security, etc.
CISSP Certification Domains

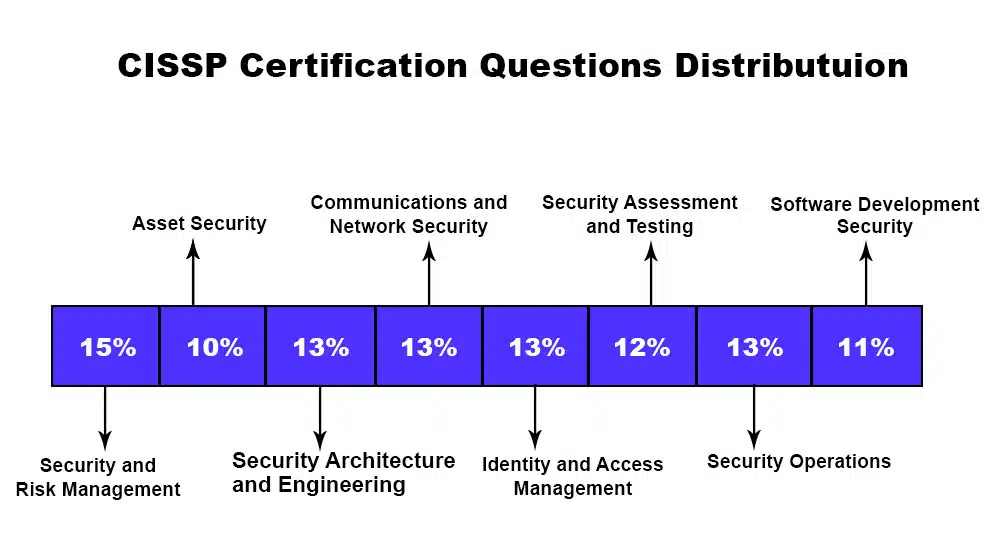
CISSP Common Body of Knowledge (CBK) includes eight CISSP domains focusing on planning and maintaining a company’s security structure.
These domains include:
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communications and Network Security
- Identity and Access Management
- Security Assessment and Testing
- Security Operations
- Software Development Security
#1. Security and Risk Management
About 15% of the CISSP test questions are from this domain. This is the primary CISSP domain and describes information system management concepts.
This domain covers:
- Calculation of observance requirements
- Compliance requirements
- Creating a scope, proposal, and strategy for enterprise continuity requirements
- IT policies and methods
- Notions of threat modeling and methods
- Risk-centered concepts
- Security control principles
#2. Asset Security
This CISSP domain focuses on resource protection and makes up 10% of the questions in the CISSP test. Asset security covers Information Management and the concept of information ownership, as well as data management, owning and processing, privacy concerns, and usage limitations.
This domain includes:
- Asset retention
- Categorization and possession of data
- Data security restrictions
- Managing requirements
- Safeguarding privacy
#3. Security Architecture and Engineering
This domain focuses on applying concepts to IS architecture design. It comprises around 13% of the CISSP test questions. It has a wide reach covering important data security topics and includes procedures, models, design guidelines, exposures, database protection, cryptosystems, and cloud computing systems.
This domain includes:
- Ability to minimize flaws in security architects, plans, web-based applications, mobile apps, and established systems.
- Cryptography
- Essential concepts of security prototypes
- Ideas for security skills of data systems
#4. Communications and Network Security
This domain focuses on establishing and maintaining network security. It comprises around 13% of the CISSP test questions.
It discusses the capacity to build dependable communication channels and network security. There are questions on diverse network design features, communication norms, separation, transmission, and wireless communications will be presented to applicants.
This domain includes:
- Applying and safeguarding layout values in network design
- Protecting communication channels
- Protecting network parts
#5. Identity and Access Management
This CISSP domain sheds light on attacks that use the human factor to get access to data and strategies to identify people authorized to connect to systems and access data. It comprises around 13% of the CISSP test questions and discusses multifactor validation, credentials, and phase conceptualization.
This domain includes:
- Approval mechanisms
- Detection and validation
- Integrating the supply of uniqueness and third-party identification services
- Logical and physical access to data
#6. Security Assessment and Testing
This CISSP domain covers the tools and techniques used to assess the security of procedures and identify flaws, mistakes in code or layout, vulnerabilities, and potentially problematic areas that policies and systems cannot address. It comprises around 12% of the CISSP test.
This domain includes
- Awareness training for clients
- Business continuity plans
- Disaster recovery
- Vulnerability assessment and penetration testing
#7. Security Operations
This domain highlights initial ideas, inspections, incident management, and disaster recovery. It comprises around 13% of the CISSP test. Digital forensics, probes, intrusion prevention and exposure tools, firewalls, and sandboxing are all included in this broad and beneficial domain.
This domain includes:
- Accumulating secure information
- Business endurance
- Enabling security inspections
- Logging and examining events
- Safeguarding the provision of assets
#8. Software Development Security
This CISSP domain focuses on how the security data system professional enforces security laws on software systems surrounded by an environment.
This domain includes:
- Detecting weaknesses in source codes
- Examining hazard evaluation
What Skills Does CISSP Certification Help Develop?
#1. Ethical Hacking
Ethical hacking shows the overall risk, vulnerabilities, and recommendations for improvement. This is done under the client’s direction. A reputable, ethical hacking curriculum is the Certified Ethical Hacker accreditation offered by EC-Council.
#2. Penetration Testing
Penetration Testing simulates a cyberattack to find weaknesses and develop plans to overcome security barriers. Early vulnerability discovery helps security teams close gaps, averting data breaches that might otherwise cost billions of dollars.
An expert-level Penetration Testing (pen-testing) certification is a Licensed Penetration Tester (LPT) developed by the EC-Council.
#3. Network Security
Network security covers numerous technologies, tools, and procedures. It describes a collection of guidelines and settings intended to safeguard the accuracy, privacy, and accessibility of computer networks and data.
The Certified Information Security Manager (CISM) is an advanced network security certification provided by the Information Systems Audit and Control Association (ISACA).
#4. Digital Forensics
A subfield of forensic science known as “digital forensic science” focuses on recovering and examining data from digital devices connected to cybercrime. It deals with the identification, preservation, analysis, and documentation of digital evidence when necessary to provide evidence in a court of law.
A Certification for Digital Forensics is the Certified Digital Forensics Examiner (CDFE).
SOC: A team of cybersecurity experts known as a Security Operations Center (SOC) is responsible for monitoring and assessing an organization’s security while responding to recent or potential breaches. Certifications for SOC are the SOC 1 and 2 Certification.
#5. Disaster Recovery
A team of cybersecurity experts is responsible for creating third-party cloud-based replication and hosting to enable complete environmental recovery in the case of a disaster. A certification for Disaster Recovery is the Disaster Recovery Certified Specialist (DRCS).
#6. Incident Response
Incident response is an organized method for dealing with different kinds of security events, online threats, and data breaches. The goal of incident response is to locate, stop, and reduce the expense of a cyberattack. An example of Incident Response certification is GIAC Certified Incident Handler (GCIH).
#7. Threat Intelligence
Threat intelligence aids in risk mitigation and involves the study of data utilizing tools and processes to produce useful information about current or potential threats aimed at the company. A certification for Threat Intelligence is the Certified Threat Intelligence Analysis provided by EC-Council.
More skills that can be developed after the CISSP certification include:
- DOS Attacks
- Cloud Security
- CCISO
- Enterprise Architect
- SQL Injection
Who Should Get the CISSP Certification?
As a young IT security expert, you may be tempted to get a CISSP certification immediately after earning a bachelor’s degree. However, there are various prerequisites to becoming a CISSP.
Candidates must have completed either five years of full-time employment or four years of employment plus an undergraduate degree (such as a bachelor’s degree in cybersecurity) or another recognized credential to be eligible for the CISSP certification.
The CISSP certification is ideal for the following professionals:
- Security Auditor
- Security Analyst
- Security Consultant
- Chief Information Security Officer
- Director of Security
- Security Manager
- Network Architect
- IT Director/Manager
- Security Systems Engineer
- Chief Information Officer
- Security Architect
How to Become CISSP Certified?
If you have the necessary expertise, study for the test and pass it. You must get at least 700 out of 1000 points to pass the test. After passing the exam, an endorsement is required from another ISC professional who can verify your professional experiences, such as employment duration, professional reputation, ongoing education as a security analyst, and subscription to the ISC Code of Ethics.
There is a yearly maintenance cost of 125 USD to keep the CISSP certification active.
CISP Certification Requirements
You must have at least five years of full-time work experience in two or more of the eight domains of the CISSP Common Body of Knowledge.
These domains are
- Security and Risk Management
- Asset Security
- Security Engineering
- Communications and Network Security
- Identity and Access Management
- Security Assessment and Testing
- Security Operations
- Software Development Security
If you hold a Graduate degree or above with eight semesters, work experience reduces to four years.
Benefits of CISSP Certification
- Fills the Knowledge Gaps: You read a lot through a structured process. This aligns your knowledge and fills your knowledge gaps.
- Global Recognition: CISSP certification is the gold standard in IT security. Employers will trust your skills and abilities, and you will be globally employable.
- Higher Salary: As shown below, the salary of a CISSP certification holder is generally more than a non-certification holder.
- More Career Opportunities: Many organizations made it mandatory to have CISSP certification to apply for IT security positions. If you hold this certification, you will get more interview calls than non-certification holders.
- Learning Opportunities: To maintain this certification, you must keep yourself updated with the latest advancements in the IT security field through Continuing Professional Education (CPE). This ensures you are always ahead in the industry with the latest knowledge and skills.
- Networking Opportunities: ISC has local chapters in many countries and cities and provides an online community on the website. You can join these communities and build your professional network to enhance your skills and find better job opportunities.
Salary of CISSP Certified Professionals
According to Global Knowledge’s 2019 IT Skills and Salary Report, North American IT workers with security certifications make 9% more money than those without certificates. The same is true for other regions, with security experts earning 6% more in Asia-Pacific, 8% more in Europe, the Middle East, and Africa (EMEA), and 13% more in Latin America.
CISSP-certified experts earn $116,573, making it the third-highest certification salary for IT experts worldwide.
Conclusion
The CISSP certification has global recognition and provides its professionals with knowledge of the latest tools, techniques, and threats in IT security. Having this certification will make you more skilled, employable, and confident.

I am Mohammad Fahad Usmani, B.E. PMP, PMI-RMP. I have been blogging on project management topics since 2011. To date, thousands of professionals have passed the PMP exam using my resources.