Risk assessment models have a crucial role in risk management practices. These risk models provide a structured framework for the risk assessment process, including identifying, analyzing, and evaluating risks and their probabilities of occurrences and impacts.
Using robust risk assessment models, you can perform risk analysis, make informed decisions, allocate resources effectively, and proactively manage risks.
This article delves into the risk assessment models and highlights their significance in risk management strategies. It will emphasize the importance of integrating risk assessment models into organizational processes to enhance risk management capabilities, foster a risk-aware culture, and achieve sustainable success.
Risk Assessment Models
The 9 most popular risk assessment models are as follows:
- Failure Mode and Effects Analysis (FMEA)
- Hazard Analysis and Critical Control Points (HACCP)
- Fault Tree Analysis (FTA)
- Event Tree Analysis (ETA)
- Bowtie Analysis
- Preliminary Hazard Analysis (PHA)
- Layer of Protection Analysis (LOPA)
- Environmental Risk Assessment Models
- Supply Chain Risk Assessment Models
#1. Failure Mode and Effects Analysis (FMEA)
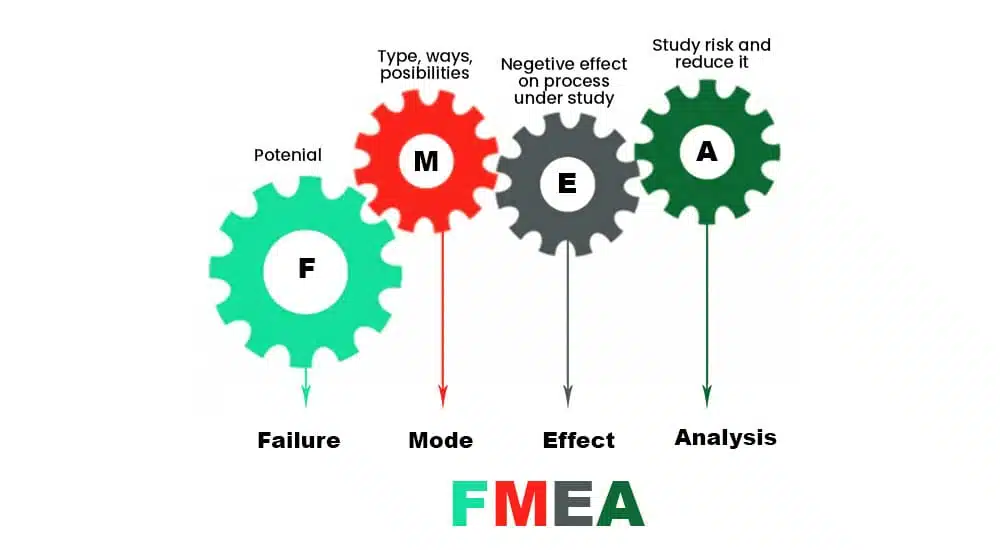
Failure Mode and Effects Analysis (FMEA) is a proactive risk assessment tool to identify and analyze system, process, or product failures. It provides a structured approach to understand the potential failure modes, causes, and effects.
FMEA can be used for hazard identification, managing risks, enhancing reliability, and improving the system’s performance.
The FMEA process involves a multidisciplinary team that collectively evaluates potential failures and their consequences using a risk matrix.
FMEA comprises the following steps:
- Identify the Scope: Define the system, process, or product that will be assessed using FMEA. Establish the boundaries and components involved in the analysis.
- Create an FMEA Worksheet: This worksheet documents the analysis. It includes columns to list failure modes, potential causes, potential effects, severity rankings, occurrence rankings, and detection rankings.
- Identify Failure Modes: Brainstorm and identify all possible failure modes within the system or process. Failure modes are specific ways the system or process can fail to meet its intended function.
- Determine Potential Causes: Identify the underlying causes or factors that could contribute to each failure mode. These causes can be design, material, process, or human factors.
- Assess Potential Effects: Determine the effects of each failure mode. Consider immediate and long-term effects on safety, quality, reliability, customer satisfaction, and other relevant factors.
- Assign Severity Rankings: Evaluate the severity or impact of each potential effect on a predefined scale. This ranking helps prioritize the critical failure modes requiring immediate attention.
- Assign Occurrence Rankings: Assess the likelihood or frequency of each potential failure mode occurring. This ranking considers factors such as historical data, expert judgment, and information to estimate the probability of occurrence.
- Assign Detection Rankings: Evaluate the ability of existing controls or detection methods to identify or prevent the failure mode. This ranking reflects the effectiveness of the current detection mechanisms in place.
- Calculate Risk Priority Number (RPN): Multiply the severity, occurrence, and detection rankings to calculate the RPN for each failure mode. The RPN helps prioritize actions by highlighting the failure modes with the highest risk levels.
- Develop Mitigation Actions: Based on the RPN values, prioritize the high-risk failure modes and develop action plans to mitigate or eliminate them. These actions include design modifications, process improvements, additional controls, or training programs.
- Implement and Monitor Actions: Execute the identified mitigation actions and monitor their effectiveness. Regularly review and update the FMEA as new information becomes available or changes are made to the system or process.
Using FMEA, you can proactively identify risks, implement preventive measures, and improve your systems or processes.
FMEA not only aids in risk mitigation but also supports decision-making, resource allocation, and overall quality improvement efforts. Its versatility and wide applicability make FMEA a valuable tool for organizations across industries, including manufacturing, healthcare, aerospace, automotive, etc.
#2. Hazard Analysis and Critical Control Points (HACCP)
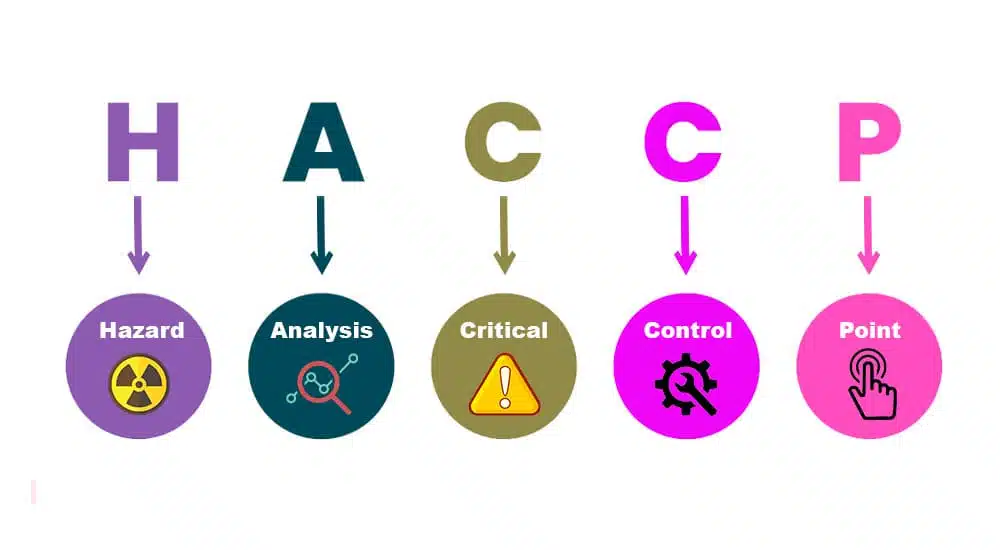
Hazard Analysis and Critical Control Points (HACCP) is a systematic and preventive approach to food safety management. It is commonly used in the food industry for identifying, evaluating, and controlling hazards that may pose risks to the safety of food products.
HACCP provides an internationally accepted framework to ensure safe and wholesome food production.
The HACCP system comprises seven core principles. These principles are as follows:
- Conduct Hazard Analysis: Identify and assess biological, chemical, and physical hazards that can occur at each stage of the food production process. Hazards include microbial contamination, allergens, chemical residues, and physical hazards like foreign objects.
- Determine Critical Control Points (CCPs): Identify the critical control points in the production process, which are steps where workplace hazards can be prevented, eliminated, or reduced to an acceptable level. CCPs are specific points where you can apply control measures to ensure food safety.
- Establish Critical Limits: Establish critical limits for each CCP, which are the criteria that must be met to ensure the control measures effectively prevent or reduce hazards. These limits may include temperature ranges, time limits, pH levels, or specific measurements.
- Establish Monitoring Procedures: Implement monitoring procedures to observe and measure the control measures at each CCP regularly. This ensures that critical limits are met, and the process is controlled.
- Establish Corrective Actions: Develop procedures for corrective actions when a deviation from critical limits occurs. These actions aim to bring the process back into control and prevent the distribution of unsafe food products.
- Establish Verification Procedures: Establish procedures to verify the effectiveness of the HACCP system. This may involve conducting periodic audits, testing samples, reviewing records, and verifying that the control measures are consistently implemented.
- Establish Record-Keeping and Documentation: Maintain records and documentation to show the implementation of the HACCP system. This includes records of hazard analysis, critical control points, monitoring results, corrective actions, and verification activities.
The HACCP requires multidisciplinary team members involving food safety experts, process engineers, microbiologists, and other relevant stakeholders. The system promotes a proactive and preventive mindset, focusing on identifying and controlling potential hazards before they occur rather than relying solely on end-product testing.
HACCP provides many benefits to the food industry, including enhanced food safety, reduced risks of food borne illnesses, increased consumer confidence, regulatory compliance, legal requirement, and improved overall quality management. The HACCP system is widely adopted globally and considered an essential tool for ensuring food safety throughout the supply chain.
It is important to note that HACCP principles can also be applied beyond the food industry. They have been adapted and used in pharmaceuticals, cosmetics, and other manufacturing processes where risk control is crucial for product safety and quality assurance.
#3. Fault Tree Analysis (FTA)
Fault Tree Analysis (FTA) is a graphical risk assessment model that identifies and analyzes combinations of events and failures that could lead to a specific undesired event.
FTA is widely used in engineering, aerospace, nuclear power, and process safety industries to identify potential failures, evaluate their probabilities, and develop risk management strategies.
It is a systematic and deductive risk assessment technique used to analyze and understand the causes of system failures. It provides a graphical representation of various events and failures that can lead to a specific undesired event or system failure.
The FTA involves the following steps:
- Define the Top Event: Identify the undesired event or system failure that will be analyzed using FTA. This top event represents the outcome to be prevented or mitigated.
- Identify Basic Events: Identify the primary events or failures that can contribute to the occurrence of the top event. These basic events are represented as nodes in the fault tree diagram, including equipment failures, human errors, external factors, etc.
- Determine Relationships and Logic Gates: Establish the logical relationships between the basic and top events. Different logic gates, such as AND, OR, and NOT, depict the relationships and dependencies between events in the fault tree.
- Assign Probabilities: Assign probabilities to the basic events, representing the likelihood of each event occurring. These probabilities can be based on historical data, expert judgment, or analysis of similar systems.
- Perform Quantitative Risk Assessment: Analyze the fault tree diagram quantitatively to calculate the overall probability of the top event occurring. This involves combining the probabilities of the basic events using the logic gates and probability rules.
- Identify Critical Contributors: Identify the critical events or failures that significantly impact the top event. These events, known as the minimal cut sets or critical paths, represent the combinations of events that lead directly to the top event.
- Develop Risk Mitigation Strategies: Based on the risk evaluation results, develop effective risk mitigation strategies to reduce the probability of critical events or failures. This may involve implementing redundancy, improving maintenance procedures, enhancing training programs, or introducing other preventive measures.
Fault Tree Analysis helps organizations understand the events and failures that can lead to system failures. FTA facilitates the identification of critical risk factors and allows organizations to prioritize their resources and efforts toward the most significant contributors to system failures.
The graphical representation of the fault tree diagram makes it easier to communicate and understand the complex relationships between events.
FTA can be used iteratively throughout a system’s design, development, and operational phases to assess and improve its reliability and safety. It supports decision-making processes by providing valuable insights into the vulnerabilities and weaknesses of a system, enabling proactive risk management and mitigation.
Fault Tree Analysis is a valuable tool for conducting risk assessments, allowing organizations to analyze and mitigate potential failures and enhance the reliability and safety of their systems and processes.
#4. Event Tree Analysis (ETA)
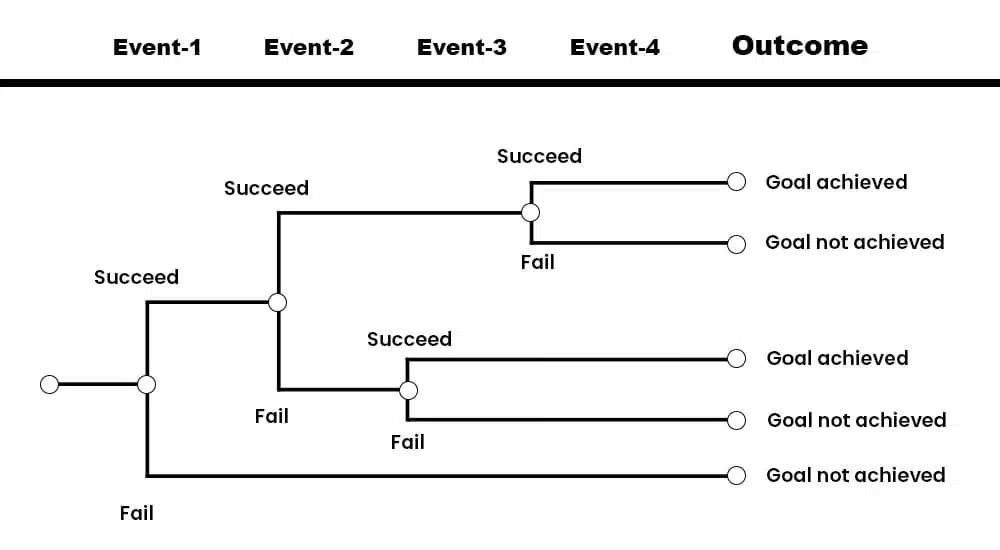
Event Tree Analysis (ETA) is a probabilistic risk assessment technique used to analyze and evaluate the consequences and outcomes of a specific initiating event or series of events.
ETA is commonly applied in nuclear power, aerospace, and process safety industries to understand the potential outcomes of accidents, failures, or other critical incidents.
The Event Tree Analysis process involves the following steps:
- Define the Initiating Event: Identify the event or set of events that serve as the starting point for the analysis. This event can be a failure, accident, natural disaster, or any other relevant incident that triggers a sequence of events.
- Identify Possible Event Sequences: Identify and describe the potential sequences of events that can follow the initiating event. These sequences represent different paths or branches in the event tree.
- Determine Event Probabilities: Assign probabilities to each event in the event tree, reflecting the likelihood of that event occurring given the preceding events. These probabilities can be based on historical data, expert judgment, or statistical analysis.
- Assess Consequences: Consequence evaluations for each event in the event tree. Consequences include human injuries, environmental damage, property damage, financial losses, or other relevant impacts.
- Develop Branching Logic: Establish the logical relationships between events in the event tree using branching logic, typically represented by AND, OR, and conditional branches. This logic determines the sequence and combinations of events that lead to specific outcomes.
- Perform Quantitative Analysis: Analyze the event tree quantitatively to calculate the probabilities of various outcomes and their consequences. This involves combining the probabilities of events along each branch and considering the probabilities of multiple branches leading to the same outcome.
- Identify Critical Paths and Cut Sets: Identify the critical paths or cut sets that lead to the most severe or significant outcomes. These paths represent the combinations of events that result in the highest risk or impact.
- Develop Risk Management Strategies: Based on the analysis, develop risk mitigation strategies to reduce the probabilities or consequences of the critical paths or cut sets. This may involve implementing safety measures, improving system design, enhancing emergency response plans, or other preventive measures.
Event Tree Analysis provides a systematic framework for evaluating complex events or accidents’ potential outcomes and consequences. It helps organizations understand the likelihood of different scenarios and their associated impacts, enabling them to prioritize resources, improve decision-making, and implement effective risk mitigation strategies.
ETA is often used with other risk assessment techniques, such as Fault Tree Analysis (FTA), to comprehensively understand complex systems or processes’ risks and potential outcomes.
By considering multiple event sequences and their probabilities, ETA helps organizations identify and focus on the most critical areas for risk management.
Event Tree Analysis is a valuable tool for assessing and managing risks. It enables organizations to proactively plan and prepare for potential events, minimize impacts, and enhance safety and resilience.
#5. Bowtie Analysis
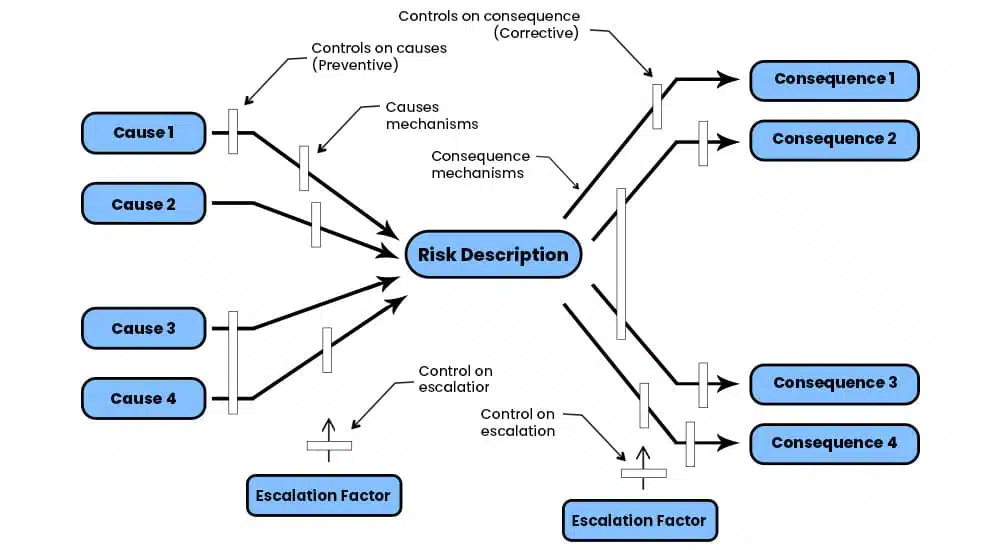
Bowtie Analysis is a risk assessment and management methodology that visually represents potential hazards, their causes, and the preventive and mitigative controls to manage those hazards. It is widely used in industries such as oil and gas, aviation, healthcare, and process safety to understand and mitigate risks associated with complex systems or activities.
The Bowtie Analysis technique gets its name from the shape of the diagram it employs, resembling a bowtie. The diagram comprises three key components:
- Hazard: The hazard represents the potential event or condition that could lead to harm, loss, or damage. It is placed at the center of the bowtie diagram and is the focus of the analysis.
- Causes: On the left side of the diagram, various causes or threats that can lead to the occurrence of the hazard are identified. These causes can include equipment failures, human errors, external factors, or other factors contributing to the hazard.
- Controls: On the right side of the diagram, preventive and mitigative controls are identified and mapped against the causes. Controls are the measures to prevent or mitigate the occurrence and consequences of the hazard. These controls can be engineering controls, administrative controls, training programs, emergency response plans, or any other risk management measures.
The Bowtie Analysis process involves the following steps:
- Identify the Hazard: Define and identify the hazard or event of concern. This can be a specific incident or potential event that poses a risk to the system, process, or activity under analysis.
- Identify Causes: Identify the various causes or threats that can lead to the occurrence of the hazard. This step involves brainstorming and listing all possible contributing factors.
- Determine Controls: Identify the preventive and mitigative controls that are in place to manage each cause. This includes identifying the control measures, procedures, systems, or strategies that can prevent or reduce the likelihood or consequences of the hazard.
- Map Controls to Causes: Connect the controls to their respective causes in the bowtie diagram, visually illustrating the relationship between causes and the controls in place.
- Assess Effectiveness: Evaluate the effectiveness of each control in managing the associated cause. This assessment can consider reliability, performance, maintenance, training, and other relevant aspects.
- Analyze Consequences: Evaluate the potential consequences of the hazard, considering the severity and impact on various aspects such as safety, environment, reputation, and financial implications.
- Identify Gaps and Improvement Opportunities: Identify gaps or areas where controls may be inadequate or ineffective in managing the hazard. This step helps to identify improvement opportunities to strengthen the risk management system.
- Develop Action Plans: Develop action plans to address the identified gaps and improvement opportunities. This may involve implementing additional controls, enhancing existing controls, improving training and procedures, or other risk reduction measures.
Bowtie Analysis visually represents the relationships between hazards, causes, and controls, facilitating better understanding and communication of organizational risks.
Bowtie Analysis helps organizations proactively manage risks, prioritize resources, and develop targeted risk mitigation strategies.
This visual risk assessment model promotes a proactive and systematic risk assessment and management approach, helping prevent incidents and enhancing overall safety and operational resilience.
#6. Preliminary Hazard Analysis (PHA)
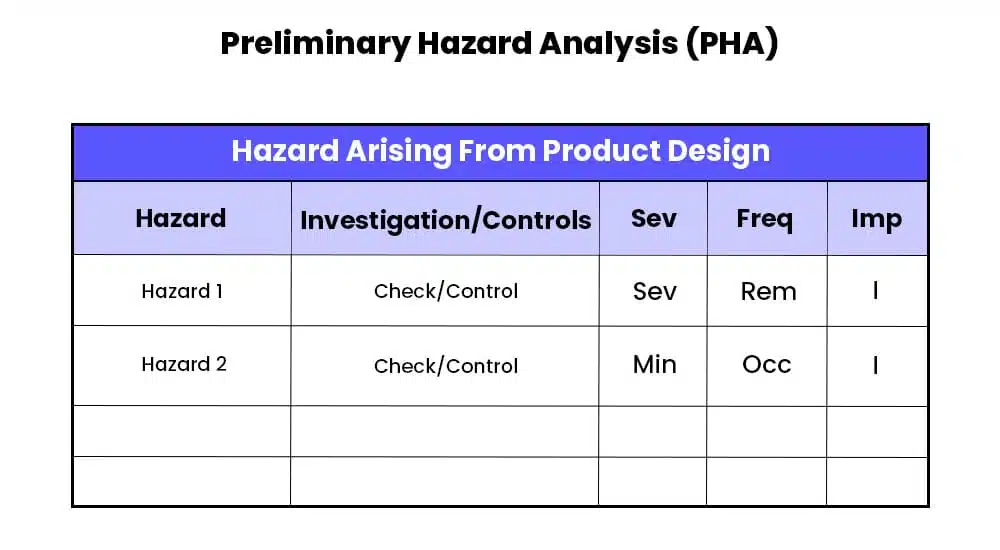
Preliminary Hazard Analysis (PHA) is a systematic and proactive risk assessment technique used to identify risks and hazards evaluations and risks associated with a system, process, or project during the early stages of development.
PHA helps organizations understand potential hazards and their consequences, enabling them to implement effective risk mitigation measures from the outset.
- Define the System or Process: Define the system, process, or project analyzed using PHA. This includes identifying the boundaries and components of the system under consideration. The Preliminary Hazard Analysis process involves the following steps:
- Identify Hazards: Identify and list potential hazards associated with the system or process. This step involves brainstorming considering various sources of hazards.
- Assess Consequences: Evaluate the potential consequences or impacts of each identified hazard. This includes considering the severity of the consequences, such as injuries, environmental damage, financial loss, or disruptions to operations.
- Determine Causes and Contributing Factors: Identify and analyze the causes and contributing factors that can lead to each hazard. This step involves understanding the underlying factors, such as design flaws, operational errors, equipment failures, or external influences.
- Evaluate Existing Controls: Evaluate the existing measures to manage the identified hazards. This includes assessing the effectiveness and adequacy of the current controls in preventing or mitigating the risks.
- Determine Risk Levels: Assess and rank the risks associated with each hazard based on the likelihood of occurrence and the severity of consequences. This helps prioritize the hazards that require immediate attention and further analysis. Risk assessors can categorize risks on rough scales such as high, medium, or low.
- Develop Risk Mitigation Strategies: Develop risk mitigation strategies and control measures based on the identified hazards and associated risks. This may involve implementing engineering controls, administrative controls, training programs, or other preventive measures to reduce the likelihood or consequences of the identified hazards.
- Document Findings: Document the findings, including the identified hazards, their causes, consequences, and recommended risk mitigation strategies. This documentation serves as a reference for further analysis and as a basis for decision-making.
Preliminary Hazard Analysis is a valuable tool for early identification and assessment of risks. It enables organizations to take proactive measures to mitigate risks, improve safety, and optimize the design and development of systems or processes.
PHA provides a foundation for more comprehensive risk assessments throughout the lifecycle of a project or system.
PHA helps organizations minimize the likelihood of accidents, incidents, or failures, leading to improved safety performance, reduced costs, and enhanced operational efficiency. PHA is valuable in the construction, manufacturing, engineering, and transportation industries, where early identification and mitigation of hazards are critical to success.
#7. Layer of Protection Analysis (LOPA)
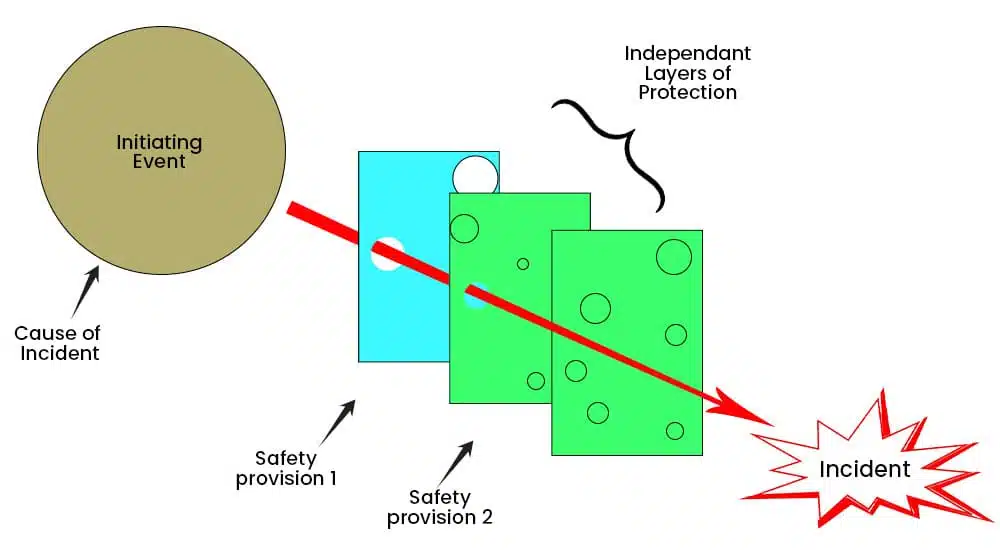
The Layer of Protection Analysis (LOPA) is a type of risk assessment technique used to evaluate and quantify the effectiveness of independent protection layers (IPLs) in reducing or preventing the occurrence of process-related hazards or accidents.
LOPA is a semi-quantitative technique commonly applied in industries such as chemical, oil and gas, and manufacturing, where multiple layers of protection are implemented to manage risks.
The LOPA process involves the following steps:
- Identify Hazard Scenarios: Identify and define the hazard scenarios that need analysis. These scenarios can include potential process upsets, equipment failures, human errors, or external events that may lead to undesired consequences.
- Determine Initial Risk: Assess the initial risk associated with each hazard. This can be done using qualitative risk assessment methods or quantitative risk analysis. Qualitative methods include expert judgment, such as historical data, and quantitative methods include probabilistic calculations, Monte Carlo analysis, sensitivity analysis, etc. Quantitative methods are also known as mathematical models.
- Identify Independent Protection Layers (IPLs): Identify the independent protection layers implemented in the system to mitigate or prevent the occurrence of hazard scenarios. IPLs can include safety systems, alarms, interlocks, relief devices, automated shutdown systems, or other risk mitigation measures.
- Assign IPL Effectiveness: Assign a measure of effectiveness (e.g., a Safety Integrity Level or a risk reduction factor) to each independent protection layer. This measure represents the ability of the IPL to reduce the risk associated with the hazard scenario.
- Calculate the Required Risk Reduction: Calculate the required risk reduction for each hazard scenario by comparing the initial risk with the tolerable or acceptable risk criteria set by the organization or regulatory standards. This determines the level of risk reduction that needs to be achieved through the IPLs.
- Determine the Adequacy of IPLs: Assess whether the IPLs can reduce the risk for each hazard scenario. This involves comparing the effectiveness of the IPLs with the required risk reduction and identifying any gaps or areas where additional protection may be necessary.
- Develop Risk Reduction Measures: If the existing IPLs are inadequate, develop risk reduction measures to fill the gaps and achieve the required risk reduction. This may involve implementing additional protection layers, improving the reliability of existing layers, or enhancing the maintenance and testing procedures.
- Document the LOPA Analysis: Document the results of the LOPA analysis, including the hazard scenarios, IPLs, their effectiveness, and the required risk reduction. This documentation serves as a basis for decision-making, ongoing risk management, and continuous improvement.
LOPA provides a systematic approach to evaluating the effectiveness of independent protection layers and ensuring that the overall risk of a process or system is kept within acceptable limits.
By analyzing the layers of protection, LOPA helps organizations optimize their risk mitigation strategies, allocate resources effectively, and enhance the safety and reliability of their operations.
LOPA is often used with other risk assessment techniques, such as Process Hazard Analysis (PHA) and HAZOP (Hazard and Operability Study), to comprehensively understand the risks and identify and prioritize risk control measures.
LOPA is a valuable tool for the risk management process, enabling organizations to make informed decisions regarding the adequacy of their protective layers and implement necessary measures to reduce risks and prevent accidents or incidents.
#8. Environmental Risk Assessment Models
Environmental risk assessment models evaluate and quantify environmental risks and impacts of human activities. These models help assess the potential consequences of various actions or projects, enabling decision-makers to make informed choices and implement effective risk management strategies to protect the environment.
Several commonly used environmental risk assessment models are:
Ecological Risk Assessment (ERA)
ERA evaluates the potential adverse effects of chemicals, contaminants, or other stressors on ecosystems and wildlife. It considers toxicity, exposure pathways, and ecological sensitivity to determine the risks of specific substances or activities.
ERA models aid in understanding the ecological consequences of pollution, habitat loss, invasive species, and other environmental stressors.
Human Health Risk Assessment (HHRA)
HHRA models assess risks to human health from exposure to environmental contaminants, such as air or water pollutants or hazardous substances. These models estimate the likelihood and severity of health effects, such as respiratory problems, cancer, or developmental disorders, based on exposure pathways, toxicity data, and population characteristics.
HHRA helps make decisions related to pollution control, land use planning, and public health protection.
Climate Change Risk Assessment
Climate change risk assessment models evaluate the impacts of climate change on various sectors, ecosystems, and communities. These models consider factors such as temperature, sea-level rise, extreme weather events, and ecological shifts to assess vulnerabilities and identify adaptation and mitigation measures.
Climate change risk assessment models aid in planning for resilience, informing policy decisions, and guiding actions to reduce greenhouse gas emissions.
Environmental Impact Assessment (EIA)
EIA is a comprehensive process that assesses the potential environmental impacts of proposed projects or developments. It considers habitat loss, water pollution, noise pollution, and socio-economic impacts.
EIA models help decision-makers understand and mitigate the adverse effects of projects, ensuring sustainable development and minimizing environmental harm.
Life Cycle Assessment (LCA)
LCA models evaluate the environmental impacts associated with the entire life cycle of a product, process, or service. It considers the extraction of raw materials, production, use, and disposal, assessing factors such as energy consumption, greenhouse gas emissions, water usage, and waste generation.
LCA models help identify eco-design opportunities, optimize resource efficiency, and guide sustainable decision-making.
Risk-Based Land Management Models
These models assess and manage risks associated with contaminated sites, land use planning, and remediation strategies. They consider soil and groundwater contamination, exposure pathways, and human health risks.
Risk-based land management models aid in prioritizing cleanup efforts, determining land use restrictions, and ensuring the safe redevelopment of contaminated areas.
#9. Supply Chain Risk Assessment Models
Supply chain risk assessment models are tools used to identify, evaluate, and mitigate risks within the supply chain. These models help organizations understand potential vulnerabilities, disruptions, and uncertainties that can impact the flow of goods, services, and information across the supply chain.
Organizations can enhance supply chain resilience, minimize disruptions, and improve overall performance by assessing and managing these risks. Here are some commonly used supply chain risk assessment models:
Failure Mode and Effects Analysis (FMEA)
FMEA is a systematic approach to identifying and prioritizing potential failures or risks within a process or system. In the supply chain risk assessment context, FMEA analyzes failure modes and their potential impacts on the supply chain.
It involves identifying failure modes, assessing their severity, the likelihood of occurrence, and detectability, and determining risk priority numbers (RPNs) to prioritize mitigation efforts.
Value at Risk (VaR)
VaR is a quantitative method used to estimate an organization’s potential financial loss due to adverse events or risks. In supply chain risk assessment, VaR helps quantify the financial impact of disruptions within the supply chain.
It considers inventory levels, lead times, demand variability, and supplier performance to estimate the potential monetary losses at different confidence levels.
Monte Carlo Simulation
Monte Carlo Simulation is a probabilistic modeling technique that simulates many possible outcomes based on input variables and their probability distributions. In supply chain risk assessment, Monte Carlo Simulation is used to assess the impact of uncertainties and risks on supply chain performance.
It helps analyze different scenarios and provides insights into potential outcomes, allowing organizations to identify critical areas and develop contingency plans.
Multi-Criteria Decision Analysis (MCDA)
MCDA is a decision-making technique that considers multiple criteria and evaluates alternatives based on their performance against these criteria. In supply chain risk assessment, MCDA helps prioritize risks and mitigation strategies by considering multiple dimensions such as the probability of occurrence, the severity of impact, the cost of mitigation, and feasibility.
It enables organizations to make informed decisions by systematically comparing and ranking various risk mitigation options.
Supply Chain Mapping and Visualization
This approach visually maps the entire supply chain network, including suppliers, manufacturers, distributors, and customers. Organizations can identify potential vulnerabilities, critical nodes, and alternative routes by visually representing the relationships and dependencies within the supply chain.
Supply chain mapping and visualization facilitate a comprehensive understanding of the supply chain and aid in identifying risks and developing risk mitigation strategies.
Business Continuity Planning (BCP)
BCP is a holistic approach to identifying and managing risks that could disrupt the operations and continuity of the supply chain. It involves assessing various risks, including natural disasters, cyber-attacks, supplier failures, and geopolitical events.
BCP helps organizations develop strategies and plans to mitigate risks, ensure business continuity, and recover quickly from disruptions.
These supply chain risk assessment models provide organizations with valuable insights into potential risks, vulnerabilities, and their potential impacts. By leveraging these models, organizations can make informed decisions, prioritize risk mitigation efforts, and enhance the resilience of their supply chains.
It enables them to proactively manage risks, ensure smoother operations, and maintain customer satisfaction despite uncertainties and disruptions.
Summary
Risk assessment models provide organizations a structured framework to identify, analyze, and evaluate risks and their impacts. By implementing effective risk assessment models, organizations can make informed decisions, allocate resources efficiently, proactively mitigate risks, and protect assets from external threats, leading to sustainable success.
Integrating risk assessment models into organizational processes enhances risk management capabilities, improves compliance with government regulations, and fosters a risk-aware culture.
Risk assessment processes are iterative, and you repeat the process using any model whenever you find new hazards.

I am Mohammad Fahad Usmani, B.E. PMP, PMI-RMP. I have been blogging on project management topics since 2011. To date, thousands of professionals have passed the PMP exam using my resources.