Certified Information Systems Security Professional (CISSP) is a globally recognized certification for experienced cyber security professionals. You can get this certification after passing a computerized test covering the eight CISSP domains, which is the core of the (ISC)2 Common Body of Knowledge (CBK).
International Information System Security Certification Consortium (ISC)2, a global non-profit organization, oversees the CISSP certification exam.
The (ISC)2 CBK guide contains knowledge and best practices in the IT industry. It also provides general vocabulary and establishes standards for information security processes. This guide helps global experts to be on the same page.
(ISC)2 was formed to collect, standardize, and maintain the (ISC)2 CBK for security specialists worldwide. The (ISC)2 domains cover a vast area designed to evaluate a candidate’s level of proficiency in information security areas.
(ISC)2 verifies applicants based on their abilities, skills, experience, and education. Their experience should cover at least two Common Body of Knowledge (CBK) domains.
The (ISC)2 CISSP CBK was officially launched in 1992, and the first CISSP certification was awarded in 1994.
What are the Eight CISSP Domains?

The eight CISSP domains are as follows:
#1. Security and Risk Management
This domain concerns the management of security risk information assets. It helps develop risk management processes and procedures.
The CISSP test will check your risk management abilities in this domain, such as risk identification, risk assessment, developing risk response, and monitoring and controlling risks.
It will also check your understanding of anti-phishing and anti-social engineering defenses and how to employ gamification to improve an organization’s cybersecurity.
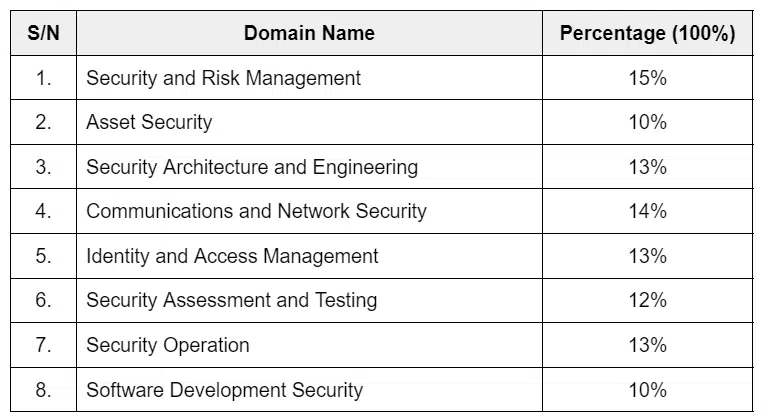
This is the biggest domain for the CISSP exam and includes 15% of exam questions.
The objectives of this domain are:
- Recognize, uphold, and support professional ethics
- Recognize and apply security concepts
- Assess and apply security governance concepts into practice
- Establish compliance and other specifications
- Understand legal and regulatory issues related to information security in a comprehensive context
- Understand requirements for investigation types (administrative, civil, criminal, regulatory, and industry standards)
- Develop, document, and use security policies, standards, procedures, and guidelines
- Define, evaluate, and rank the needs for Business Continuity (BC)
- Participate in and uphold personnel security guidelines
- Recognize and use the principles of risk management
- Recognize and use threat modeling principles and techniques
- Use the principles of Supply Chain Risk Management (SCRM)
- Establish and manage a program for security awareness, education, and training
#2. Asset Security
This domain helps an organization protect its information assets, such as software, hardware, and data. Asset security classifies information assets, designs security control measures to safeguard assets, and manages physical and logical access to critical assets.
In the exam, this domain verifies an applicant’s understanding of the various data handling responsibilities (owner, controller, and custodian), data security techniques, and data states. It contains the skills necessary for various vocations in data management, ownership, and processing, as well as privacy issues and usage restrictions.
This domain includes 10% of exam questions.
The objectives of this domain are:
- Identify and categorize assets and information
- Create guidelines for information and asset handling
- Securely provision resources
- Manage the lifespan of data
- Make sure to retain assets acceptably [end-of-life (EOL) and end-of-support (EOS)]
- Determine the compliance requirements (DRM, CASB, and DLP) and data security procedures
#3. Security Architecture and Engineering
This domain helps design and apply secure systems and networks. Topics of this CISSP domain are security models, security controls, mitigating information system risks, access control systems, and cryptography.
This sector also includes virtualized systems, cloud systems, and system infiltrations (including ransomware, fault injection, and more).
It includes 13% of exam questions.
The objectives of this domain are:
- Investigate, put into practice, and oversee engineering procedures utilizing safe design principles
- Recognize the underlying ideas behind security models
- Select controls per the needs for system security
- Recognize the capabilities of information systems security (IS)
- Evaluate and address the vulnerabilities of security architecture, design, and solution components
- Determine and choose cryptographic methods
- Recognize how cryptanalytic assaults are conducted
- Designing a location and facility with security in mind
- Create sites and building security measures
#4. Communication and Network Security
This domain secures an organization’s communication and network system. Topics include secure communication protocols, network security devices, and network design.
This domain will test your knowledge of securing networks and communication channels in the CISSP exam. Other covered topics are secure and convergent protocols, wireless and cellular networks, hardware operations (warranty and redundant power), third-party connections, etc.
IPSec, IPv4, and IPv6 networking are also included in this domain.
It includes 14% of exam questions.
The objectives of this domain are:
- Evaluate and implement secure design concepts in network architectures.
- Reliable network elements.
- Implement secure communication methods following plan
#5. Identity and Access Management (IAM)
This domain involves managing human user identities, controlling their access to the system, and protecting information assets from attacks.
This domain covers user account management, authentication methods, and authorization controls.
It assesses whether candidates can recognize people who have access permissions to servers and information. Application, single sign-on authentication, privilege escalation, Kerberos, rule-based or risk-based access control, proofing, and identity setup are also included within this domain.
It includes 13% of exam questions.
The objectives of this domain are:
- Control access to assets, physically and logically
- Manage people, devices, and service identity and authentication
- Federated identity using a service from a third party
- Establish and control permission procedures
- Control the provisioning lifecycle for identities and access
- Install authentication methods
#6. Security Assessment and Testing
This domain evaluates an organization’s security posture and testing of the security control and system. This domain covers vulnerability assessment, penetration testing, and security testing methods.
It helps analyze methods and instruments used to identify system flaws, weaknesses, and possible problems that security protocols and rules do not cover. This domain includes ethical disclosure and attack simulations.
The test will check candidates for vulnerability analysis and penetration testing. Compliance checks are also included.
It includes 12% of exam questions.
The objectives of this domain are:
- Create and verify assessment, testing, and auditing procedures
- Test security control procedures
- Gather data about security procedures (technical and administrative)
- Examine test results and produce a report
- Carry out or assist with security audits
#7. Security Operations
Security operations cover the daily operations of an organization’s security systems and processes. This domain covers security management, incident management, and disaster recovery.
Analytics of user and entity behavior, threat intelligence (threat hunting and threat feeds), log management, artifacts (mobile, computer, and network), and tools based on machine learning and artificial intelligence are also included.
This domain includes 13% of exam questions.
The objectives of this domain are:
- Recognize investigations and follow their guidelines
- Perform logging and monitoring tasks
- Manage your setup
- Implement basic security operational principles
- Use resource protection
- Manage incidents as needed
- Run and maintain surveillance and security systems
- Implement and support patch and vulnerability management
- Recognize the procedures of change management and take part in them
- Implement recovery plans
- Implement procedures for Disaster Recovery (DR)
- Test Disaster Recovery strategies
- Take part in planning and testing for Business Continuity (BC)
- Manage physical security implementation
- Address issues with staff security and safety
#8. Software Development Security
The Software development security domain involves the integration of security into the software development process. It covers secure software design, secure coding practices, and software testing for security.
Risk analysis, vulnerability spotting, and source code auditing are also included.
The test examines candidates for open-source and third-party development security, maturity models, development techniques, and software-built security.
This domain includes 10% of exam questions.
The objectives of this domain are:
- Recognize security issues and include them in the Software Development Life Cycle (SDLC)
- Identify security controls in software development ecosystems and implement them
- Programming languages, toolkits, runtimes, IDEs, continuous delivery automation and response, continuous integration, application security testing, and dynamic application security testing
- Evaluate how well software security works
- Evaluate the impact of purchased software on security
- Define and use secure coding standards and guidelines
Beginning June 1, 2022, the CISSP exam in the Computerized Adaptive Testing (CAT) format will contain 50 pretests (unscored) items, which will increase the minimum and the maximum number of items you will need to respond to from 100-150 to 125-175 items during your exam. The maximum exam administration time will increase from three to four hours to allow for these additional items. (Source)
To pass the test, the applicant must have a score of at least 70%.
The following table shows the question distribution in each CISSP domain.
Summary
The CISSP domains are the basis for the CISSP certification exam and provide comprehensive knowledge of skills required to protect organizational information assets and secure the system.

I am Mohammad Fahad Usmani, B.E. PMP, PMI-RMP. I have been blogging on project management topics since 2011. To date, thousands of professionals have passed the PMP exam using my resources.